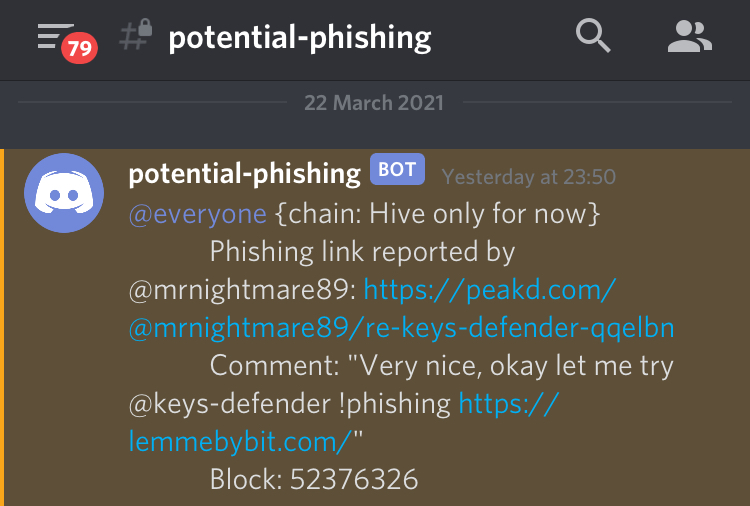
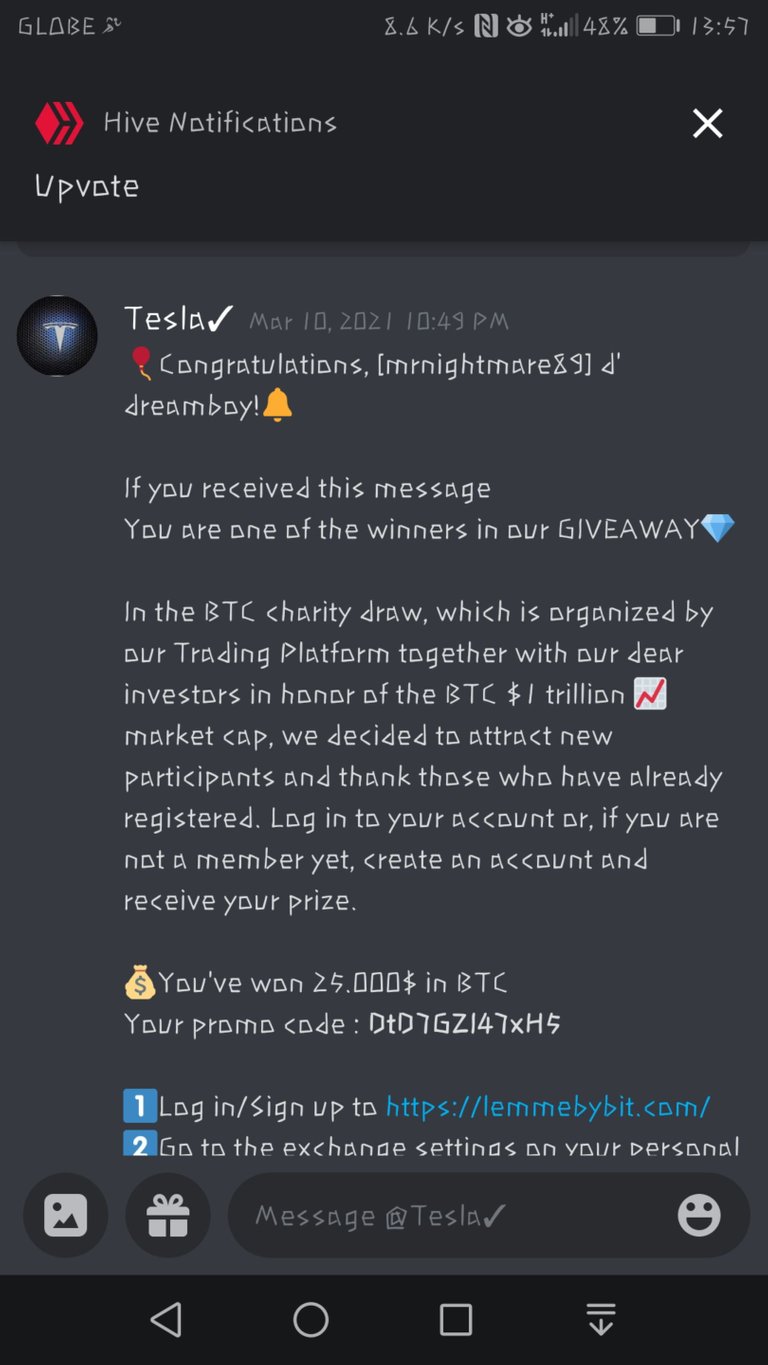
Following up on the previous work I did to counteract phishing (1. auto-replies and 2. universal script to block phishing links in all Hive frontends) I now present a way for the Hive community to actively participate and timely stop phishing campaigns.
How does it work?
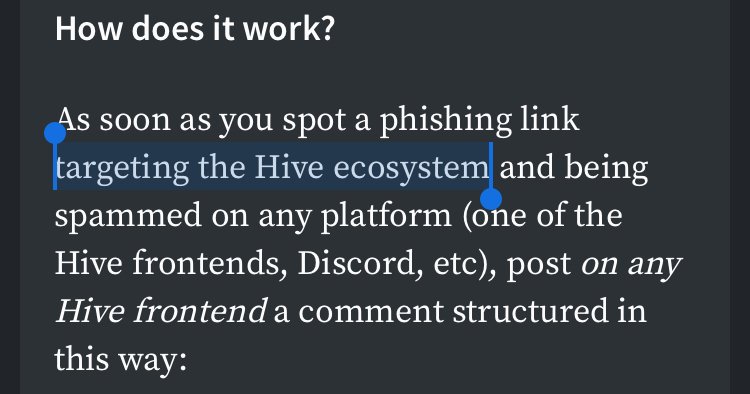
As soon as you spot a phishing link targeting the Hive ecosystem and being spammed on any platform (one of the Hive frontends, Discord, etc), post on any Hive frontend a comment structured in this way:
- Mention @keys-defender
- Include the command "!phishing"
- Add the phishing link - eg. https://givemeallyourhoney.com/airdrop
Outcome: @keys-defender will add the reported phishing domain to its banlist and it will immediately start replying to the phishing comments and counteracting the transfer memos in order to timely warn users against the phishing campaign.
Usage example:
https://hive.blog/hive-148441/@keys-defender/qq9fz0
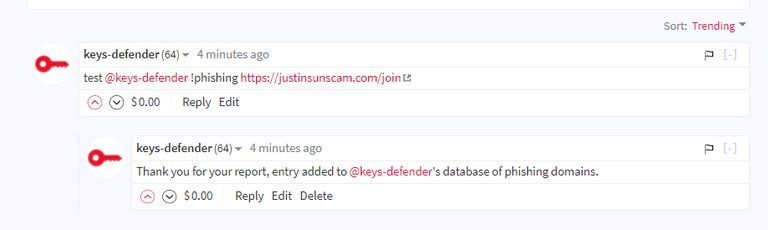
Who controls the banlist?
Can anyone add a domain to the banlist? Kind of. In order to prevent abuse, some limitations are in place.
The type of users that are able to immediately blacklist a domain are:
(apologies for the mass tag)
- myself 👈
- Any top-40 witness 👉
- Any trusted user - current list 👇
@gaottantacinque, @hivewatchers, @hivewatcher, @spaminator, @enforcer48, @logic, @joshman, @shmooglesukami, @penguinpablo, @jlsplatts, @splatts, @anthonyadavisii, @steevc, @hiveseph,
@louis88, @saboin, @memehub, @antisocialist, @reazuliqbal, @r0nd0n, @edicted, @slobberchops, @taskmaster4450, @aggroed, @tarazkp, @drutter, @solominer, @steemseph
Any other regular user can add domains to the banlist too BUT.. at least 3 reports from different users with a reputation above 50 are required in order for the entry to be automatically added to the banlist.
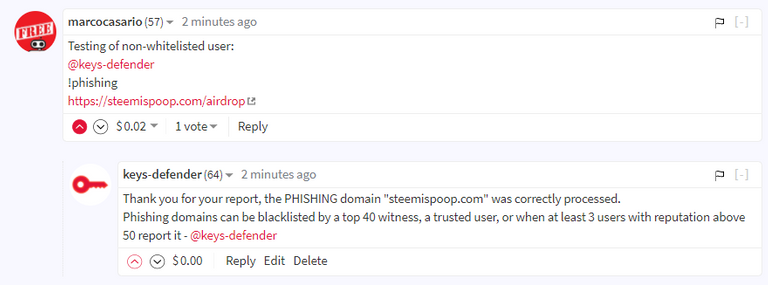
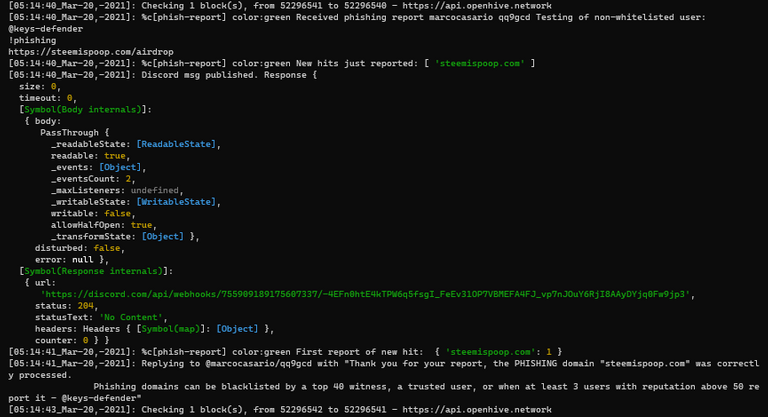
https://hive.blog/hive-148441/@marcocasario/qq9gcd
Perks:
Every report gets a ~ $ 0.25 upvote.
(Users that abuse this feature will get heavy downvotes from me and my flag trail)
Futher countermeasures and Tracking:
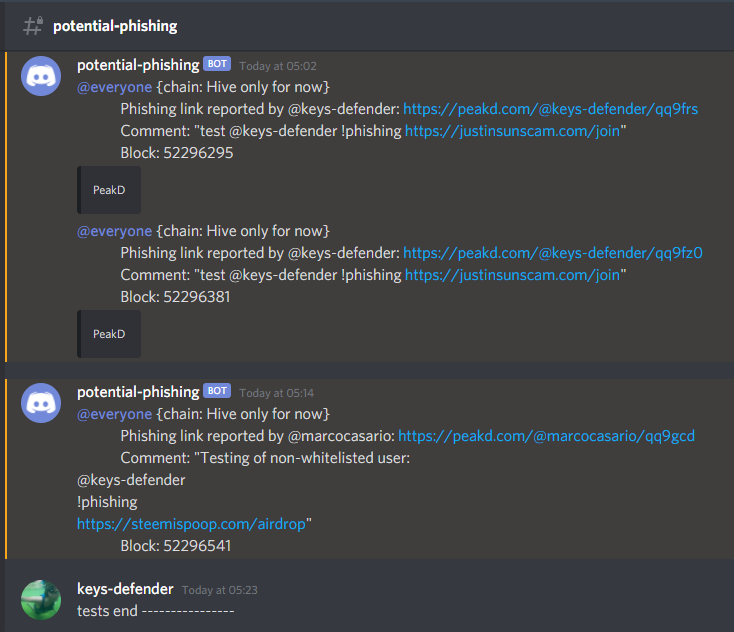
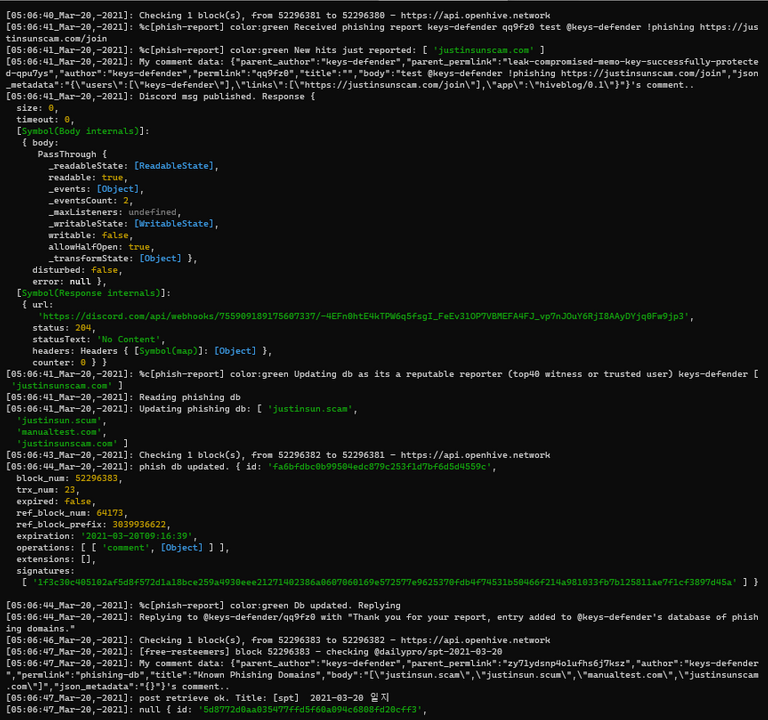
Every single report triggers a notification to my Discord server.
This allows me and the other volunteers (with a role assigned) in my discord to take action - eg. contact the hosting service to take the phishing website down.
This also allows us to have a record of who reported what (and every report is immutably stored in the Hive blockchain for everyone to see).
Where is the banlist stored?
It's stored in the Hive blockchain itself -> https://hive.blog/hive-193084/@keys-defender/phishing-db
To see all the changes performed to it over time check out: Hive Scribe or Hive-DB

Whitelist:
What if a rogue user tries to ban a legit domain just to cause trouble?
To prevent such scenario there is a domains whitelist in place. Meaning that if for example an attacker controlling 3 accounts with reputation above 50 tries to add to the banlist peakd.com in order to cause mass spam from @keys-defender, they won't be able to.

Future development:
The list of community reported phishing domains is now in use by @keys-defender, meaning that after a domain gets added to the banlist, @keys-defender will immediately start replying to any new comment containing that link.
The next step is to update and release a new version of my universal script for hive frontends so that all Hive frontends using it will not only consume @spaminator's api (that still needs a quick fix), but also @guiltyparties's banlist and mine.
My phishing domains banlist will be an initial copy of @spaminator's plus all the community reported links.

Testers required
Test plan:
A. Myself blacklisting a domain - PASSED
B1. My non-whitelisted alt account with reputation above 50 reporting the testing domain https://steemispoop.com - PASSED
B2. 2 more accounts with reputation above 50 reporting https://steemispoop.com - PASSED
C. 1 account with reputation below 50 reporting a link - PASSED
D. 1 top-40 witness reporting the testing domain https://phish-test-domain1.com - PASSED
E. 1 whitelisted user reporting the testing domain https://phish-test-domain2.com - PASSED
F. Any account reporting a phishing link and forgetting to add the link (ie. "@keys-defender !phishing") - PASSED
G. Any account not including the mention to @keys-defender (PS. now supported) and reporting a phishing link already known - PASSED
H. Any account posting a comment with a link that has just been put in the banlist by other users - PASSED
PS. All tests are now successful, thanks everyone!
- XSS vulnerabilities in #########.com
- XSS vulnerabilities in hive-db.com
- XSS vulnerabilities in scribe.hivekings.com
- XSS vulnerabilities in hiveblockexplorer.com
- Malicious ads redirecting all Steemit iOS users to a phishing site
- Reverse tabnabbing and clickjacking in steem.chat and steeemit registration page
Other contributions:
- Universal script to prevent phishing in all Hive frontends
- Commands for community reports and ban lists
Keys-Defender features:
- Phishing protection [live scan of commentsa and posts to warn users against known phishing campaigns and compromised domains, scan of memos]
- Re-posting detection [mitigates the issue of re-posters]
- Code injections detection [live scan of blocks for malicious code targeting dapps of the Hive ecosystem]
- Anti spam efforts [counteracts spam from hive haters]
Take care, @keys-defender (@gaottantacinque)